ADCS Installation Guide
Installation
After successful installation and configuration of domain controller setup. we need to install the ADCS from Add Roles and Feautures
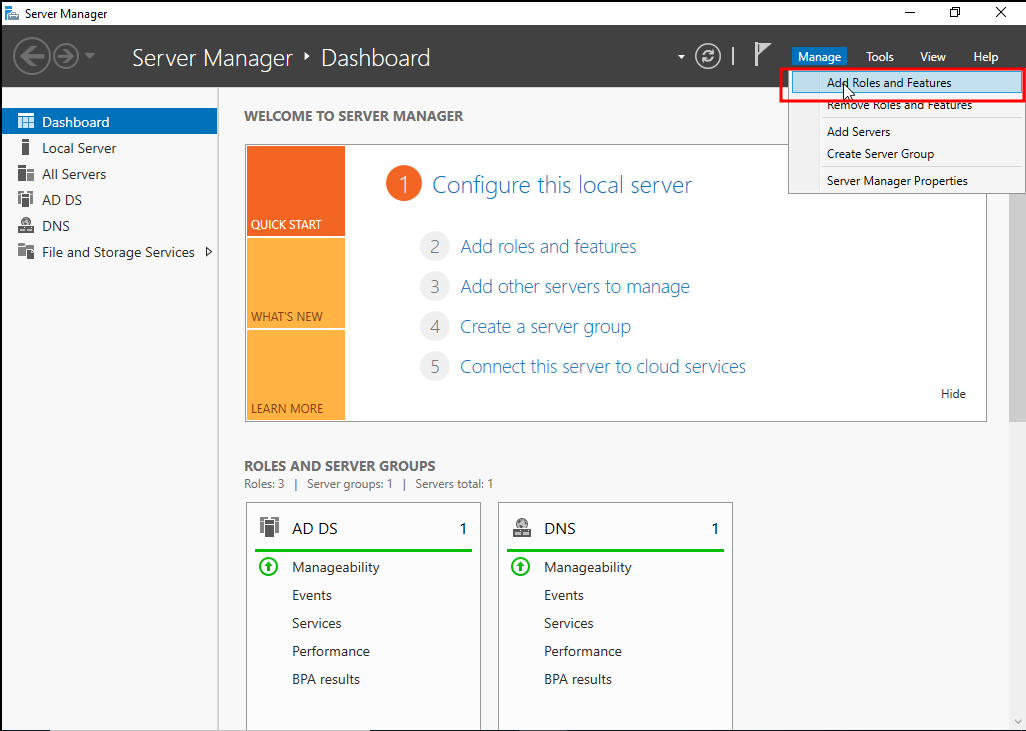
The installation wizard comes up after we clicked to the Add Roles and Feautures
we simply clicked next at the begin page.
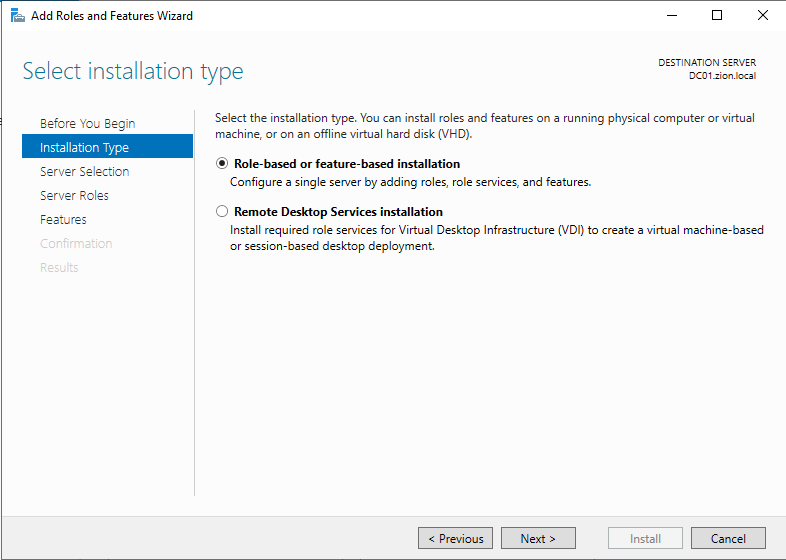
at the Installation Type section we should chose the Role-based type
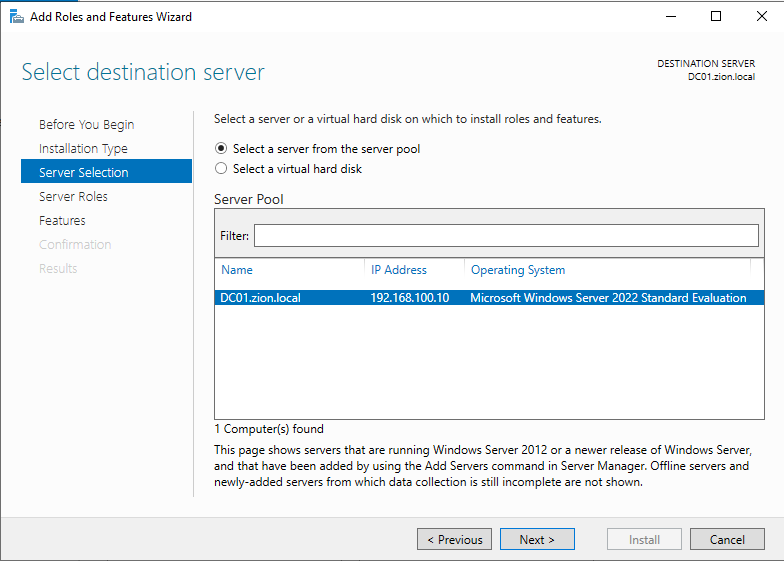
at the Server Selection section we are choosing our DC.
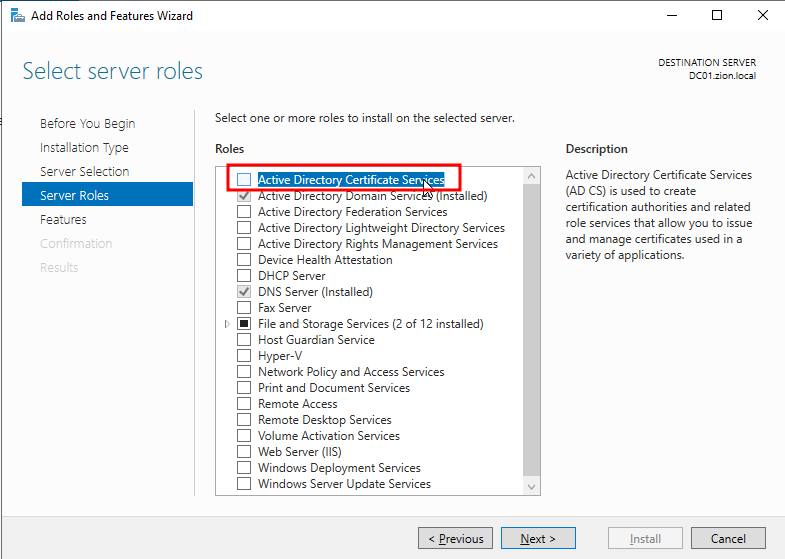
at the Server Roles section we should check the ADCS box to install.
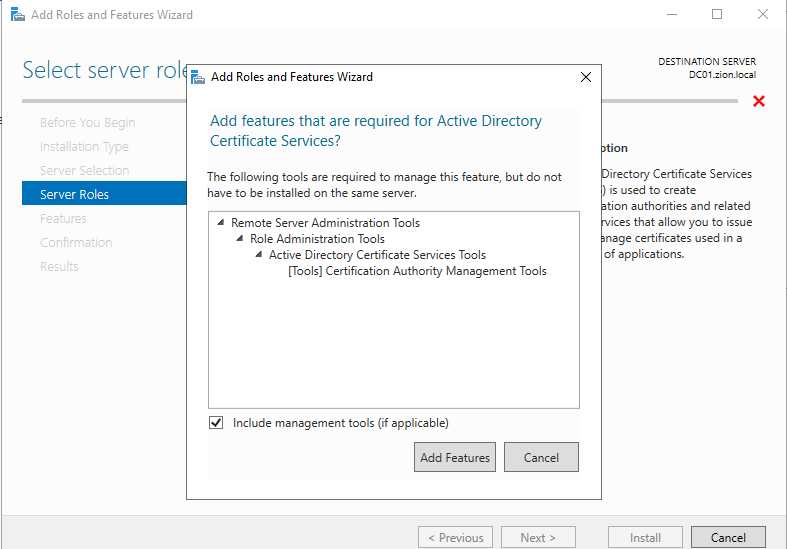
clicked Add Features
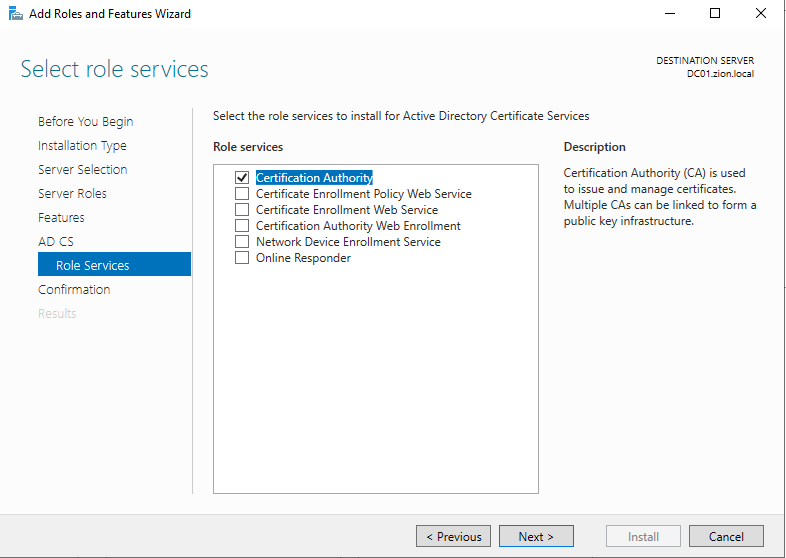
Then we need to chose role services. For now we can choose only the Certificate Authority to just install the CA and default templates. If we want to install other role services we can come back later to install.
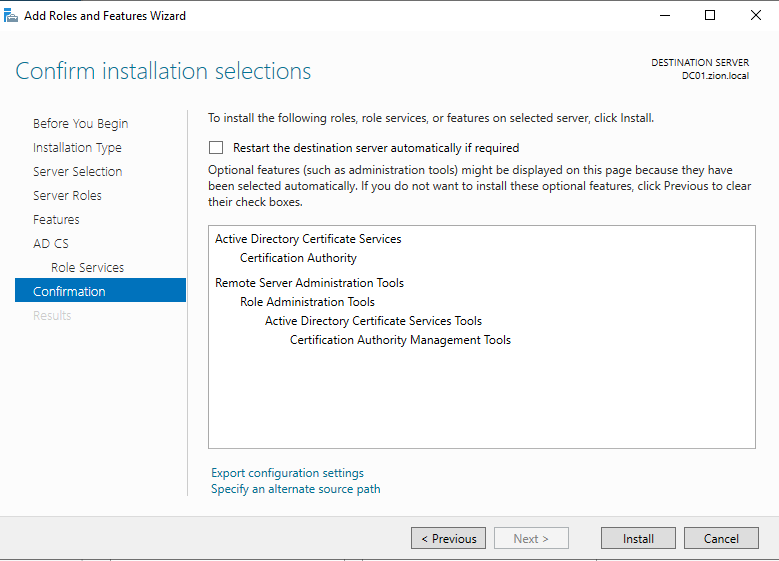
And lastly we confirm our selections and clicked install.
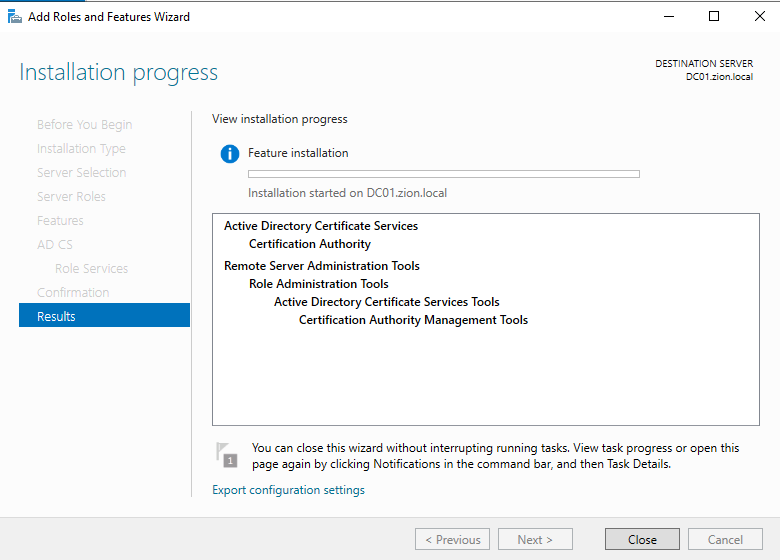
Configuration
After installation ends. At the top of the Server Manager we should have a notification. After the install we need to configure the ADCS like ADDS.
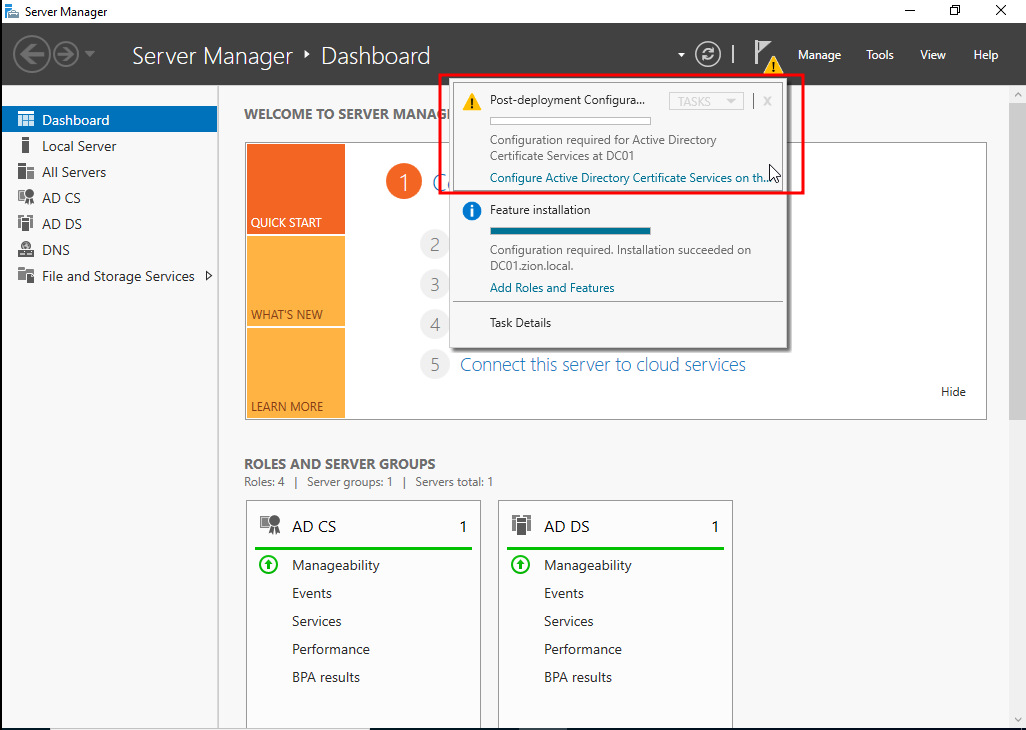
We clicked to Configure Active Directory Certificate Services
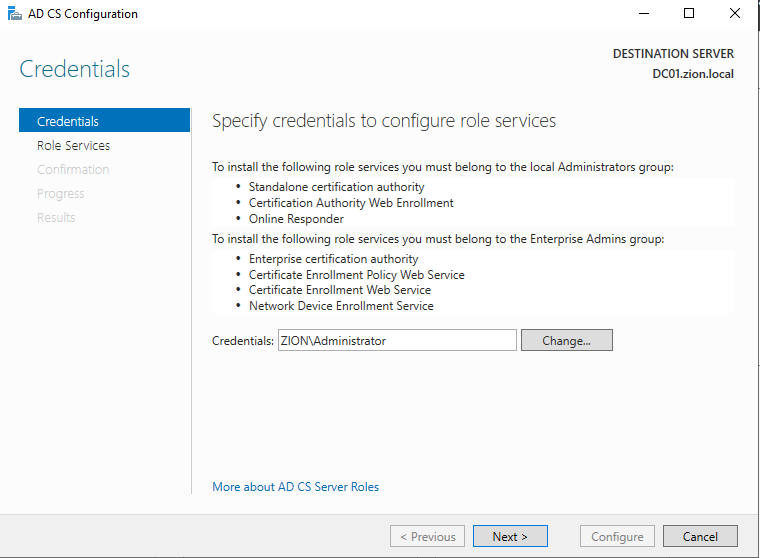
And the configuration wizard comes up. It asks for privileged user but automatically gets the our admin user.
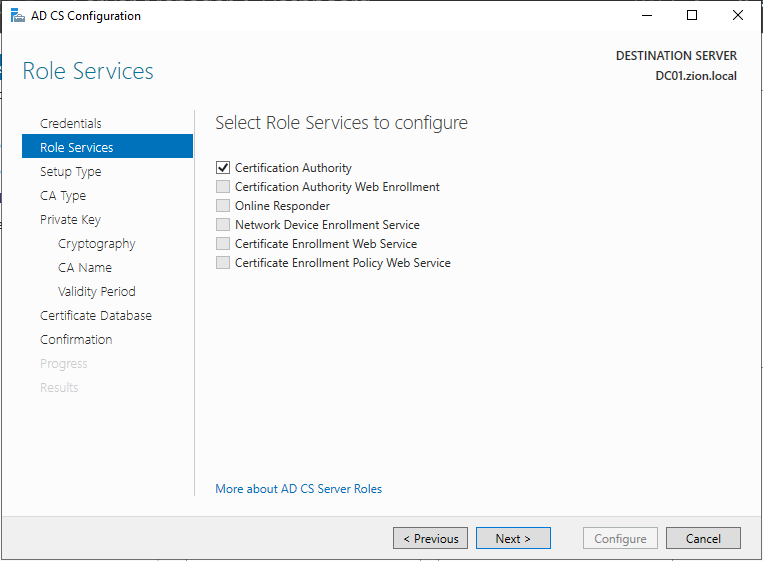
We choose the CA for configure and clicked next
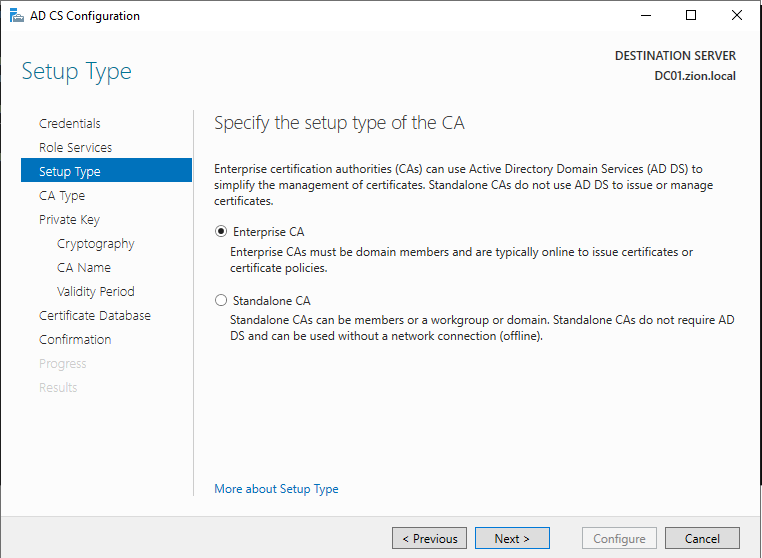
At Setup Type section its important to choose Enterprise CA if we are working in a domain.
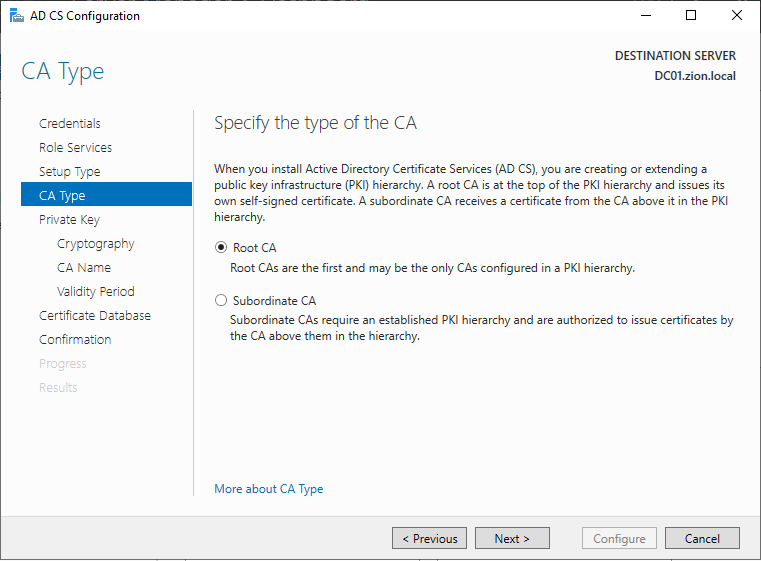
Choosing the Root CA at CA Type section
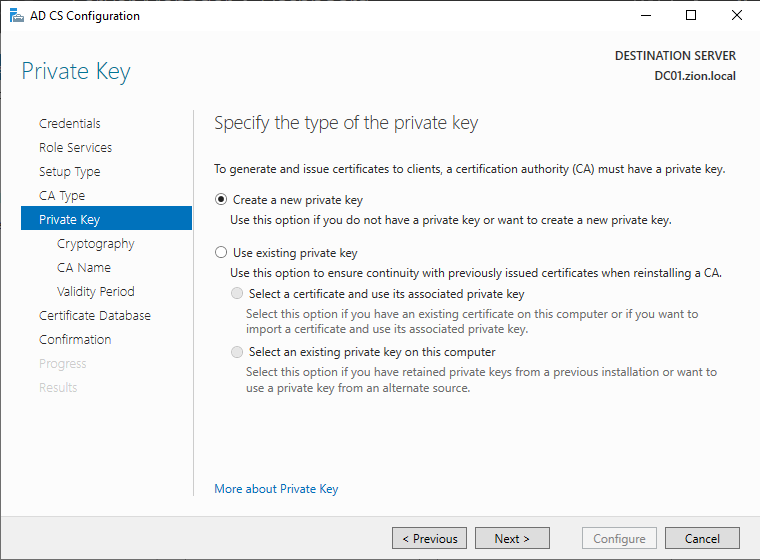
If we are creating a new CA we can choose the Create a new private key option. This will create our root CA’s private key to use forge operations.
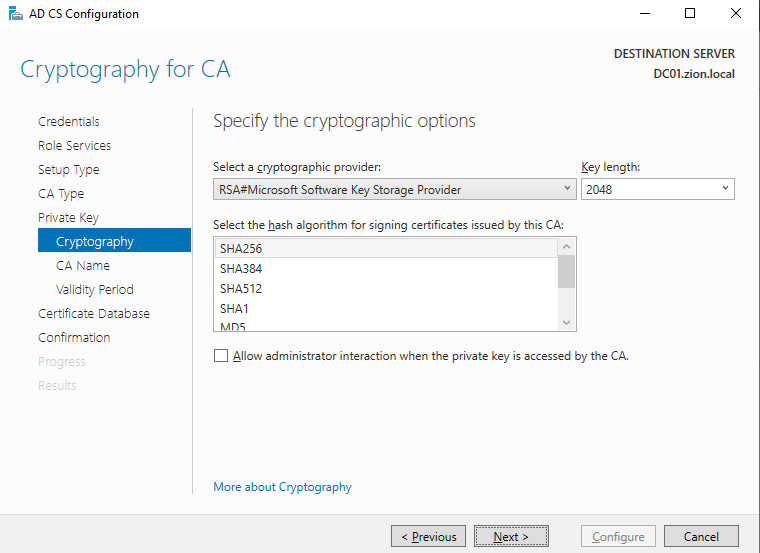
Cryptoghraphy section can stay as default settings, after the install we can change it if we want.
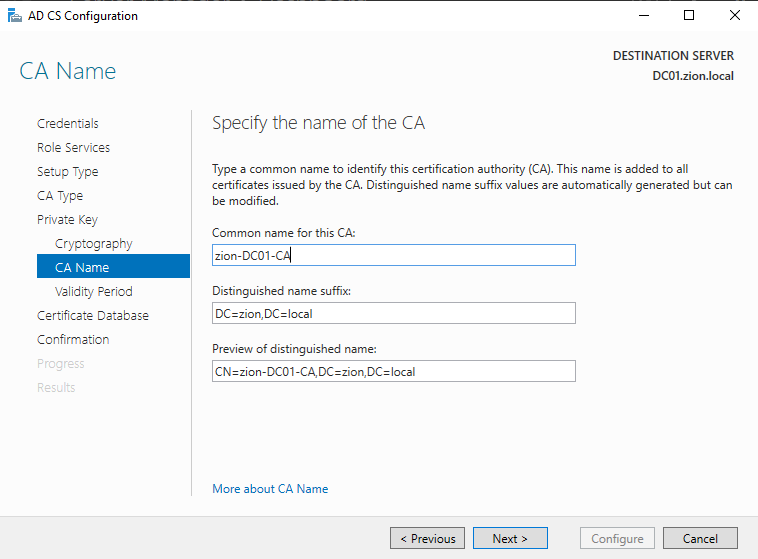
CA Name section is defines the DN names and the CA Names for communation in the domain structure. we can set as default the CA Name or change if we want.
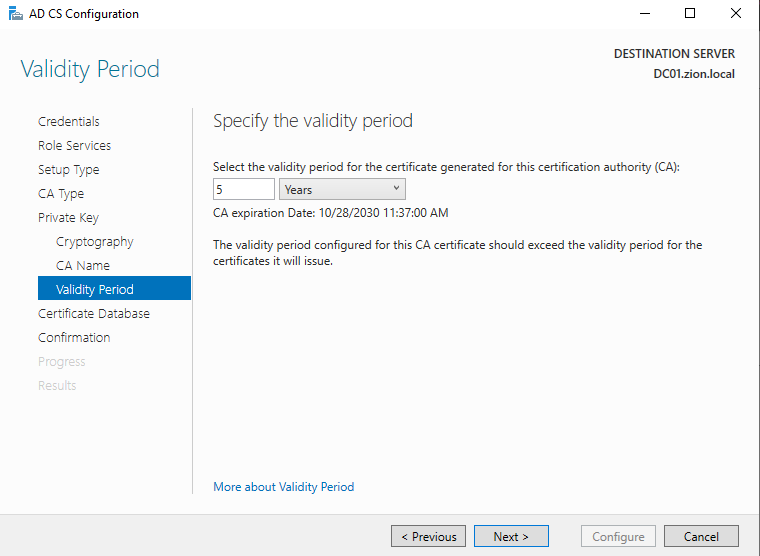
Validity Period section defines the life time of the generated certs. This setting by default comes with 5 years. What a persistence method to use :D.
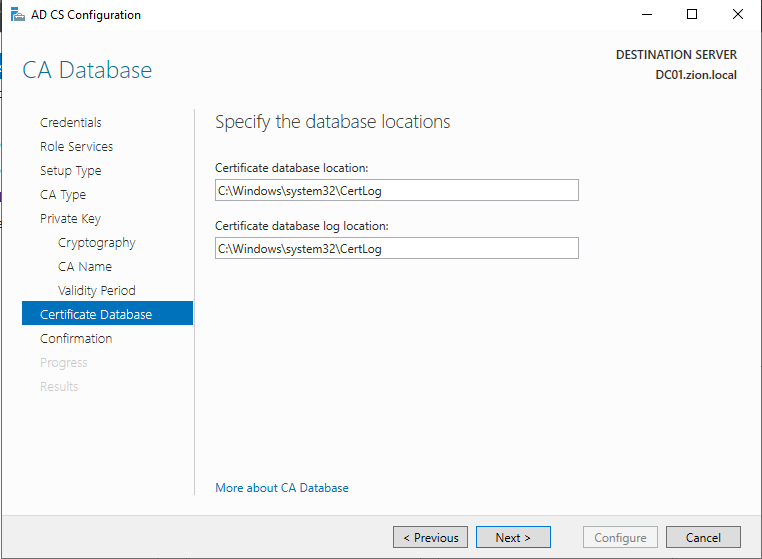
Certificate Database section defines the location of the databases. we can set it by default too.
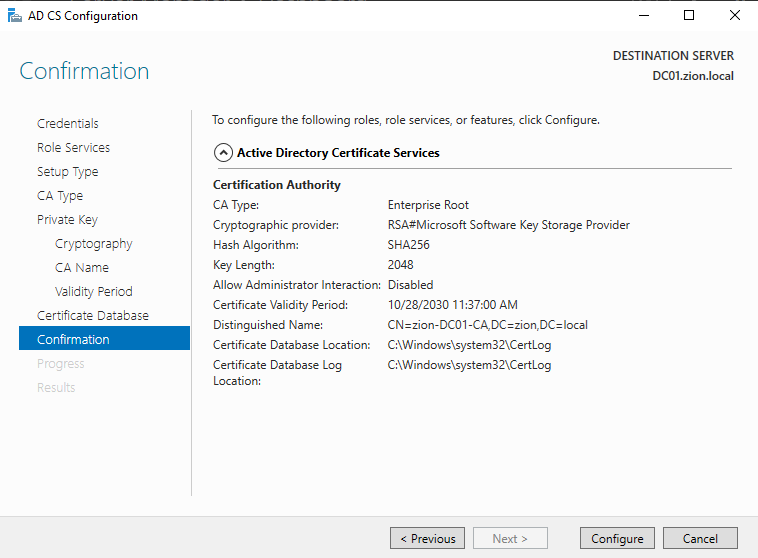
At the Confirmation section we take a look to the settings and clicked to configure.
Configuring process started.
Configuring process succeeded.
Check
After the setup process we can check the CA with any domain user.
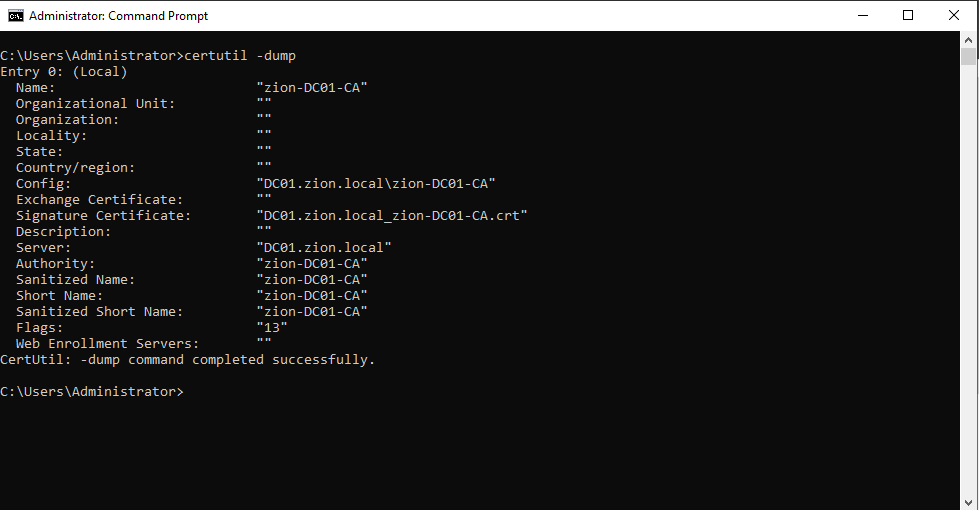
certutil -dump
This command shows us the basic information about the ADCS.
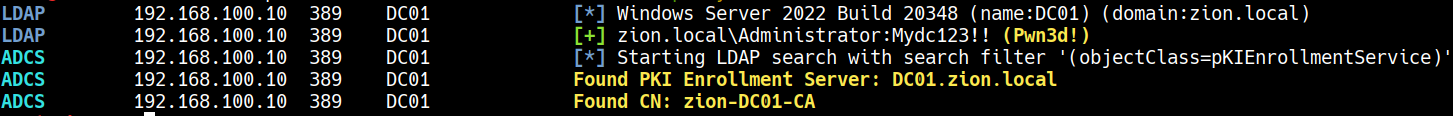
We can check the ADCS with network joined linux too via netexec
netexec ldap 192.168.100.10 -u Administrator -p <pass> -M adcs
we can check for the templates with certutil
certutil -Template
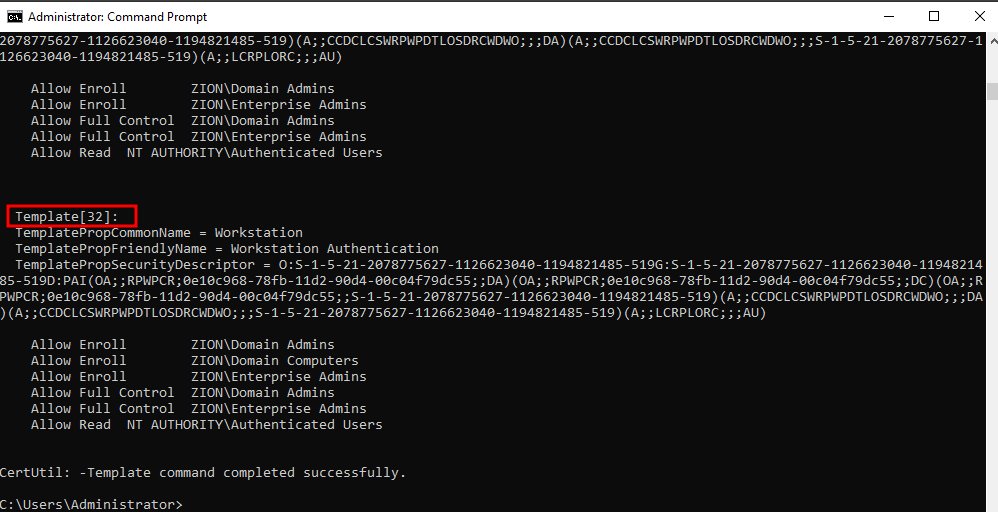
As we can see we got 32 templates by default.